Feb17
40 Million Credit Cards — V.
Editor’s Note
The image may be downloaded in higher resolutions:
↓ Transcript
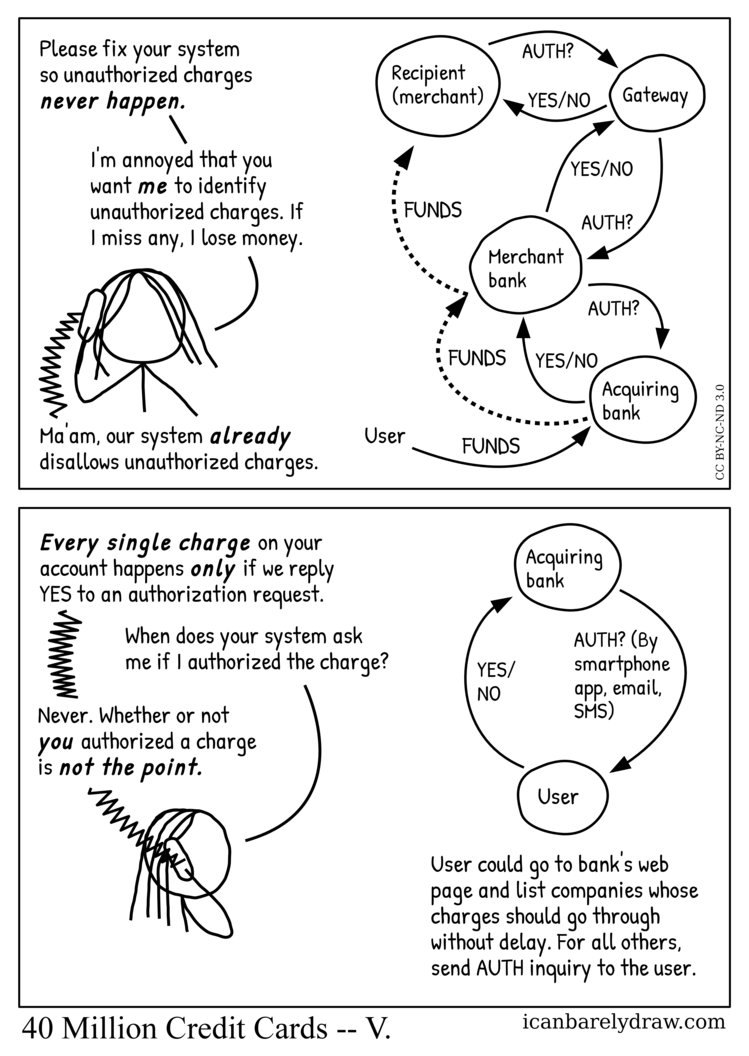
A woman is talkng on the phone.
Woman: Please fix your system so unauthorized charges never happen.
Woman: I'm annoyed that you want me to identify unauthorized charges. If I miss any, I lose money.
Voice from phone: Ma'am, our system already disallows unauthorized charges.
Accompanying the above dialog, a diagram shows AUTH? requests going from Recipient (merchant) to Gateway to Merchant bank to Acquiring bank. Replies of the form YES/NO take the reverse path. Also shown are FUNDS going from User to Acquiring bank to Merchant bank to Recipient (Merchant).
The dialog continues in the second and final panel.
Voice from phone: Every single charge on your account happens only if we reply YES to an authorization request.
Woman: When does your system ask me if I authorized the charge?
Voice from phone: Never. Whether or not you authorized a charge is not the point.
An accompanying diagram shows a request going from Acquiring bank to User. This request is: AUTH? (By smartphone app, email, SMS).
A reply of the form YES/NO goes in the reverse direction.
Text below this diagram says: User could go to bank's web page and list companies whose charges should go through without delay. For all others, send AUTH inquiry to the user.
Title: 40 Million Credit Cards -- V.
Woman: Please fix your system so unauthorized charges never happen.
Woman: I'm annoyed that you want me to identify unauthorized charges. If I miss any, I lose money.
Voice from phone: Ma'am, our system already disallows unauthorized charges.
Accompanying the above dialog, a diagram shows AUTH? requests going from Recipient (merchant) to Gateway to Merchant bank to Acquiring bank. Replies of the form YES/NO take the reverse path. Also shown are FUNDS going from User to Acquiring bank to Merchant bank to Recipient (Merchant).
The dialog continues in the second and final panel.
Voice from phone: Every single charge on your account happens only if we reply YES to an authorization request.
Woman: When does your system ask me if I authorized the charge?
Voice from phone: Never. Whether or not you authorized a charge is not the point.
An accompanying diagram shows a request going from Acquiring bank to User. This request is: AUTH? (By smartphone app, email, SMS).
A reply of the form YES/NO goes in the reverse direction.
Text below this diagram says: User could go to bank's web page and list companies whose charges should go through without delay. For all others, send AUTH inquiry to the user.
Title: 40 Million Credit Cards -- V.